How Our Decentralized Design Protects Your Identity

People talk about hedging their bets — not putting all their eggs in one basket, diversifying their portfolio to mitigate risk.
So why don’t we apply the same logic we use for financial decisions to our personal data?
Why do we still hand over our private information to individual corporations for the sake of “verification,” trusting them to handle it responsibly?
When a single entity controls all of your data, you’re at their mercy — and any cracks in their system could have devastating consequences for you.
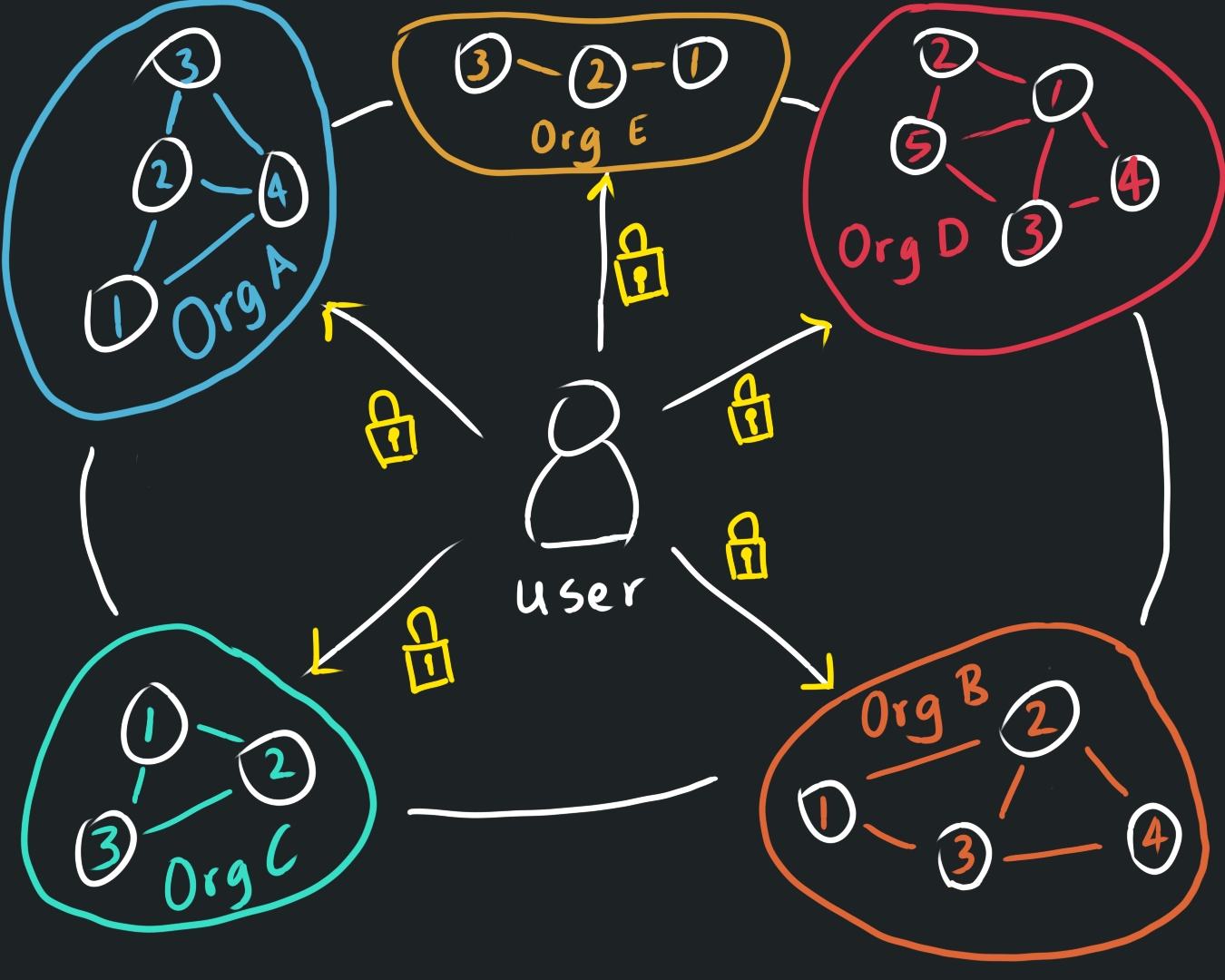
The solution? Decentralization.
By encrypting your data and splitting the encryption key into pieces stored across multiple independent and trustworthy nodes, we create a system where no one entity ever has complete control over your data — yet you can still securely verify your identity online.
The beauty of this distributed design is resilience. Even if one node or server is compromised, your full data remains safe, because there’s no single point of failure. A hacker would need to breach multiple nodes across the entire network — something far more difficult than attacking a centralized database.
A distributed approach also protects against bad actors within the network. Each node only stores encrypted fragments of data, meaningless on their own. So even if someone running a node tried to access your information, they wouldn’t be able to.
Trust in such a network comes from the fact that access to data isn’t controlled by a single authority — it’s divided among independent nodes in the network.
Our implementation lets users place their trust not in us as developers, but in the design itself — in the principles of decentralization.
Decentralization gives people back control over their own data — and that’s a major step toward restoring trust in how identity is verified online.